Introduction
Imagine building a thriving business, surviving recessions, adapting with technology, and employing hundreds of people – with an annual turnover of £94 million, more than £100,000 a year is spent on IT and cyber security. Then overnight, that’s all taken away. The company goes into administration. Operations cease, and hundreds of jobs are lost. All due to a cyber security incident. How can that be?
In this article, we delve into the importance of multi-factor authentication (MFA), reference relevant case studies, make connections to the Cyber Essentials scheme and explain why Cyber Essentials Plus testing can be of huge benefit to organisations.
Background
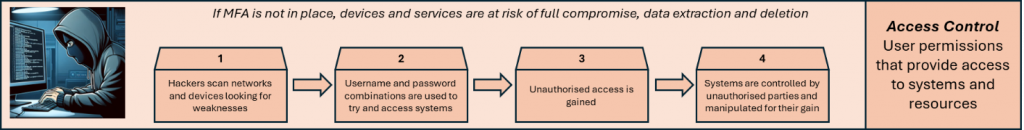
With cyber security-related attacks growing more sophisticated every day, organisations must be prepared for the threat of unauthorised access. One of the most effective ways to strengthen defences is through the deployment of MFA – a security control that requires more than just a username and password combination to access systems. MFA can reduce the risk of account compromise, even when credentials have been leaked or stolen.
Increasingly, threat actors target internet-based login portals, trying out different usernames and passwords to gain access (called a brute force attack). Without MFA, credentials that have been stolen from other network hacks (called credential stuffing), or simply just guessed, can provide threat actors with unauthorised access.
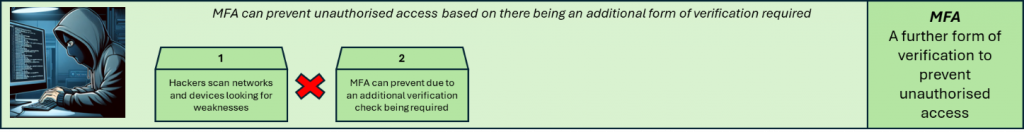
MFA adds an additional level of protection, so that further information is required before providing access. That’s something other than a username and password. This means that if the correct username and password combination is identified, a further challenge is made to help protect access to data and systems. That additional protection can be in the form of a mobile authenticator app challenge, facial recognition, fingerprint, hardware token, or email code – something that’s going to be a lot harder to guess or establish.
Cyber Essentials includes MFA as a core requirement for cloud services and administrator accounts, recognising its value in protecting organisations from common internet-based threats. With Cyber Essentials Plus, active testing ensures that MFA has been correctly enforced. Test findings are often revealing — exposing instances where MFA is disabled, misconfigured, or inconsistently applied across users or devices. These gaps might not be immediately visible, but they represent real risks — it could be a key service that’s unprotected, providing access to organisational data.
MFA can therefore be one of the most reliable lines of defence in a constantly shifting threat landscape.
What is MFA?
Cyber Essentials Requirements for IT Infrastructure V3.2, states that MFA provides “an extra layer of security for passwords that aren’t protected by the other technical controls. You should always use multifactor authentication to give administrative accounts extra security, and accounts that are accessible from the internet. Effectively, MFA is like an extra lock on a door and window – making them more secure are harder to break into. By applying MFA, organisations can reduce risk and avoid costly security issues. MFA can be an essential step towards the prevention of a major incident.
Acceptable forms of MFA listed in the Cyber Essentials Requirements for IT Infrastructure V3.2 are:
- “a managed / enterprise device
- an app on a trusted device
- a physically separate token
- a known or trusted account”
There’s also an important information statement in the IT Requirements document: “SMS is not the most secure type of MFA, but still offers a huge advantage over not using any MFA at all. Any multi-factor authentication is better than not having it at all. However, if there are alternatives available that will work for your situation, we recommend you use these instead of SMS.”
Example Case Study 1
In September 2023, BBC News reported that Knights of Old, a £100M UK logistics firm, had collapsed following a ransomware attack. Despite spending over £100,000 annually on IT and cyber security. The breach involved the deployment of ransomware, resulting in corrupted financial data, halted operations, and led to the administration, impacting 730 jobs. A review by CyberSecurityNews concluded, “Multifactor authentication enforced for all remote access and cloud apps—is essential.”
Example Case Study 2
On 16th April 2025, a penalty notice for £60,000 was released by the Information Commissioners Office (ICO), relating to a cyber attack on a law firm in Merseyside (DPP Law Ltd). The attack related to a brute force technique, where the username and password are guessed based on trial and error. The report reinforced the use of MFA to support cyber security, noting that “At the time of the incident, DPP had MFA for the purposes of connecting to its network. However, the administrator account did not have MFA due to its role as a service-based account.”
How Can Cyber Essentials Help?
The Cyber Essentials scheme provides organisations with a framework of effective security measures. The scheme requires organisations to implement user access control, implementing MFA where available, especially for cloud services and administrator-level accounts. By following these requirements, organisations can reduce risk, protect data, and demonstrate good security practice. It’s not just about passing a test, it’s about taking action that will make it harder for hackers to break in and cause damage.
Why is Cyber Essentials Plus a Benefit to Organisations?
Cyber Essentials Plus offers additional benefits with hands-on testing and verification. MFA is checked for all cloud services – for user and administrator-related accounts. This testing can identify misconfigurations that attackers could easily exploit. The testing provides organisations with extra confidence that defences are working in practice, not just on paper. By ensuring MFA is in place for cloud services, organisations can reduce risk and protect customer data.
Successful Attacks Even with MFA in Place
It’s important to add that even though MFA is an effective security measure, attackers can still bypass it using different techniques. MFA fatigue involves bombarding users with repeated login prompts until one is approved out of frustration. Token theft allows attackers to steal session tokens via malware or phishing, granting access without triggering MFA. Machine-in-the-middle attacks intercept login credentials (and MFA codes) in real-time, using fake websites and proxies. Incorrect MFA implementation, social engineering, and SIM swapping can also contribute to successful breaches. Regardless, MFA remains an extremely effective preventative measure and should be implemented wherever possible.
How We Help
At RB Consultancy Ltd, we support organisations looking to implement controls and/or certify to Cyber Essentials and Cyber Essentials Plus requirements:
- As Cyber Advisor, we help organisations understand and implement technical controls and provide detailed steps on how to resolve this vulnerability
- As a Cyber Essentials Plus Assessor, we assess organisations against the requirements, ensuring MFA is in place for cloud services
- As a Cyber Essentials Plus Certification Body, we issue certifications to successful applicants
Conclusion – Why MFA is so important
Multi-factor authentication (MFA) is a key security control that significantly enhances the protection of data and systems. By requiring multiple forms of verification, MFA reduces the risk of unauthorised access, even if credentials are compromised. The implementation of MFA, as highlighted by the Cyber Essentials scheme, is essential for safeguarding against common cyber threats. Real-world examples, such as the collapse of Knights of Old and the cyber-attack on DPP Law Ltd, highlight the importance of MFA as a security measure. Cyber Essentials Plus can provide organisations with extra assurances relating to access control, with MFA being checked for all cloud services as part of the testing.
Written by Remo Belisari, Managing Director of RB Consultancy Ltd, an experienced cyber security professional and cyber advisor. Remo holds certifications relating to CISSP, ISSAP, ISO 27001, Cyber Essentials, IASME Cyber Assurance, and has many years experience in IT and cyber security. Remo has a history of supporting organisations from over the world – including a Fortune 500 in USA and over 100 organisations across the UK. The views expressed in this blog are those of the author and do not necessarily reflect the views of RB Consultancy Ltd, its clients, partners, or affiliated organisations. The content is intended for general information only.

