Introduction
Imagine hackers scanning the internet, looking for access. They’re using artificial intelligence and machine learning to automate and speed up their processes. They find a missing security patch, an outdated system or a misconfiguration to gain a foothold. They make their way to the data and copy it to their own location. They try to destroy backups and then encrypt systems. This can be a major incident. Normal operations could be impacted. Days (weeks) could be spent on recovery. But then it could get worse…
The data that was copied by the attackers could be leaked on the internet – double-extortion. This could have a major impact on clients and partners. It could be personal and sensitive data, leading to emotional and psychological impact. The Information Commissioner’s Office (ICO) could be involved and carry out an investigation, issuing a public notice and a financial penalty. This isn’t just your imagination – this is just the type of thing that can happen if vulnerabilities and weaknesses are not identified and remediated.
In this article, we explore the term ‘vulnerability fixes’, explain what they are, and set out why they’re so important. We make reference to an example case study, make connections to the Cyber Essentials scheme and explain why Cyber Essentials Plus testing can be of huge benefit to organisations.
Background
With more vulnerabilities being discovered every day, organisations can stay manage this type of threat through effective vulnerability management. Being aware of security risks, applying updates, patches, and device hardening techniques, can help reduce risk and avoid a data breach. Vulnerability assessments identify security weaknesses, which can often go unnoticed (despite applying regular Windows updates). An ongoing cycle of thoroughly checking and applying vulnerability fixes is a great defence based on this changing threat landscape.
Cyber Essentials has secure configuration and security updates as key elements of the scheme, aimed at protecting organisations from common forms of internet-based attack. Critical and high-risk security updates must be applied within 14 days, and secure configurations must be in place. For Cyber Essentials Plus, active testing takes place to identify whether an internet-based opportunist can hack into a system with low skill methods. Deep vulnerability assessments are also carried out on servers and end-user devices to help identify missing patches and weaknesses, which could be exploited by bad actors. Findings are extremely valuable and aren’t always visible – they could be associated with registry settings on a Windows device or an open port on a firewall, providing open access to people and tools that know where to look.
What are Vulnerability Fixes?
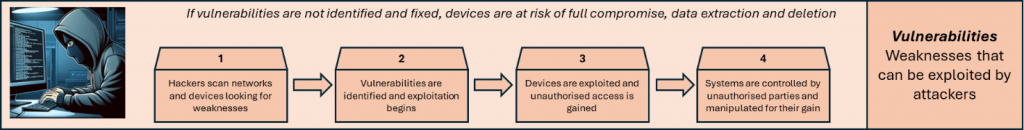
Cyber Essentials Requirements for IT Infrastructure V3.2 states that “vulnerability fixes include patches, updates, registry fixes, configuration changes, scripts or any other mechanism approved by the vendor to fix a known vulnerability”. Effectively, they’re actions are taken to secure open doors and windows. By finding and fixing vulnerabilities early, organisations reduce risk and avoid costly security issues. The application of vulnerability fixes is therefore an essential step towards the prevention of a major incident.
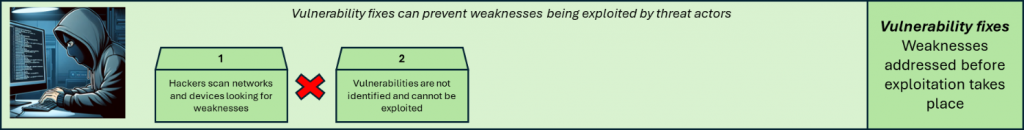
Example Case Study
On 26th March 2025, a penalty notice for over £3 million was released by the Information Commissioners Office (ICO). This followed an investigation of a security incident relating to Advanced Computer Software Group Limited. The ICO review determined that there was a “failure to undertake adequate vulnerability scanning within the environment”. The ICO also determined that there was a “failure to have adequate patch management in place to ensure the ongoing confidentiality, integrity and availability of data”. The £3 million penalty notice was just part of the financial impact, with the report stating, “Advanced submits the overall incident remediation and response costs were in excess of £21 million.”
How Can Cyber Essentials Help?
The Cyber Essentials scheme provides organisations with a way to apply effective security measures – through five key technical controls. The scheme requires organisations to apply vulnerability fixes to common weaknesses, like outdated software or missing patches. Critical and high risks need to have vulnerability fixes applied within 14 days of vendor notice, with the intention being to prevent attackers from exploiting these weaknesses (the sooner the fix is applied, the better). By following these requirements, organisations can reduce risk, protect data, and demonstrate good security practice. It’s not just about certification, though – it’s about taking action that will make it harder for hackers to break in and cause damage.
Why is Cyber Essentials Plus a Benefit to Organisations?
Cyber Essentials Plus offers additional benefits with hands-on testing and verification. Through detailed vulnerability assessments, led by experts in their field, the testing can uncover hidden weaknesses. Often the testing can identify outdated software or misconfigurations that may go unnoticed, but that attackers could spot and exploit. It gives organisations extra confidence that defences are working in practice, not just on paper. By fixing issues before they become an issue, organisations can reduce risk and protect customer data. Cyber Essentials Plus is not just about certification – it’s a proactive step to support cyber security protection and smooth business operations.
What Tools are Used for Cyber Essentials Plus Testing?
For Cyber Essentials Plus, trusted tools are used to check how secure systems really are. The tools are similar to those used for payment card industry testing. This includes vulnerability assessment software that can identify where vulnerability fixes should be applied. Checks are made on end-user devices, servers, and internet-based network equipment. Assessors use specific tools to inspect devices. These tools don’t make changes – they report what’s there, raise awareness of risks, and help drive remediation.
What Information is Gathered By the Cyber Essentials Plus Testing Tools?
The vulnerability tools focus on system security. They gather technical details such as software versions, missing updates, open ports, and basic device configurations. These tools help identify weaknesses that hackers could exploit. They operate in read-only mode, and their purpose is to check whether systems are secure.
Successful Attacks with Vulnerability Fixes Applied
Fixing vulnerabilities is essential, but it doesn’t prevent all attacks from being successful. Threat actors can exploit unknown or zero-day vulnerabilities, where a patch is not yet available. Exploits can take place between the time that a patch has become available and the time at which it was applied. Configurations may also be applied incorrectly, leading to system exposure and exploitation. Regardless, applying vulnerability fixes is an essential step for cybersecurity hygiene and best practice, and can be vital in reducing the risk of security breaches.
How We Help
At RB Consultancy Ltd, we support organisations looking to implement controls and/or certify to Cyber Essentials and Cyber Essentials Plus requirements:
- As Cyber Advisor, we help organisations understand and implement technical controls and provide detailed steps on how to resolve this vulnerability
- As a Cyber Essentials Plus Assessor, we assess organisations against the requirements, using tools designed to identify vulnerabilities and weaknesses
- As a Cyber Essentials Plus Certification Body, we issue certifications to successful applicants
Conclusion – Why vulnerability fixes are so important
Today’s attackers are constantly looking for vulnerabilities, using artificial intelligence and machine learning to hunt for weaknesses faster than ever. An unpatched or misconfiguration device could be all it takes for a threat actor to exploit a system, often quietly and unnoticed. Personal and sensitive data, business reputation, and customer trust could all be impacted. Significant penalties can be imposed by the Information Commissioners Office for ineffective vulnerability fixes. Costs of recovering from security incidents can add significantly more costs. But there are ways to defend against this type of attack.
By applying vulnerability fixes and replacing outdated systems, organisations can aim to address weaknesses before they’re exploited. By applying updates and secure configurations, organisations can gain protection from common forms of cyber-attack. One key benefit of Cyber Essentials is quick security updates. High and critical risks must be fixed within 14 days. Cyber Essentials Plus adds scans and assessments to find weaknesses. These help raise awareness and drive remediation. Vulnerability fixes are so important. It’s not just about compliance with a scheme and certification – it’s about raising awareness, having an effective process, and protecting what matters.
RB Consultancy Ltd help organisations understand the importance of vulnerability fixes – we support the implementation of appropriate measures to support cyber security. We are an IASME Certification Body and Assured Service Provider who provide services to empower and protect organisations. Contact Us for assistance with cybersecurity.
Written by Remo Belisari, Managing Director of RB Consultancy Ltd, an experienced cyber security professional and cyber advisor. Remo holds certifications relating to CISSP, ISSAP, ISO 27001, Cyber Essentials, IASME Cyber Assurance, and has many years experience in IT and cyber security. Remo has a history of supporting organisations from over the world – including a Fortune 500 in USA and over 100 organisations across the UK. The views expressed in this blog are those of the author and do not necessarily reflect the views of RB Consultancy Ltd, its clients, partners, or affiliated organisations. The content is intended for general information only.

