
Cyber Security Risk Management: Protecting Against Supply Chain Security Risks
Effective cyber security risk management is not about eliminating every threat – it’s about understanding what could go wrong and putting appropriate measures in place to protect what matters most. The 2020 SolarWinds attack exposed critical supply chain security risks, with thousands of organisations compromised through a trusted vendor. It acts as a cautionary tale on how cyber defences can be bypassed and how cyber resilience could be improved through effective supply chain risk management. With the UK government recently recommending Cyber Essentials certification throughout the supply chain of the FTSE 350, this could also act as a timely reminder on how external threats (from outside the organisation) should be carefully considered and managed.
Scenario
Imagine your organisation is thriving. Teams are productive, systems are stable, and customers are happy. Everything feels under control. Then it happens….
One morning, a routine software update triggers unexpected behaviour. Systems slow down. Files vanish. Staff report strange activity. You suspect a cyber incident, but there’s no clear evidence. Days pass. Then the truth is exposed – attackers have exploited a weakness that had never been assessed. Sensitive data has been stolen. Regulators are notified. The impact is costly.
This isn’t just imagination – it mirrors the reality of the SolarWinds supply chain attack, where thousands of organisations were compromised through a trusted vendor. The breach can be used to learn valuable lessons from and links to the topic of effective risk management.
In this article, we focus on the theme of risk and explore how it contributes to cyber resilience. We reference a case study, provide general guidance and recommendations.
What is Risk?
Risk is about understanding the likelihood and impact of threats, managing them accordingly. It’s about putting measures in place to reduce risk to an acceptable level. It’s a continual process that can be built on over time – with appropriate controls being applied to reduce the likelihood of a weakness being exploited and preventing significant impacts.
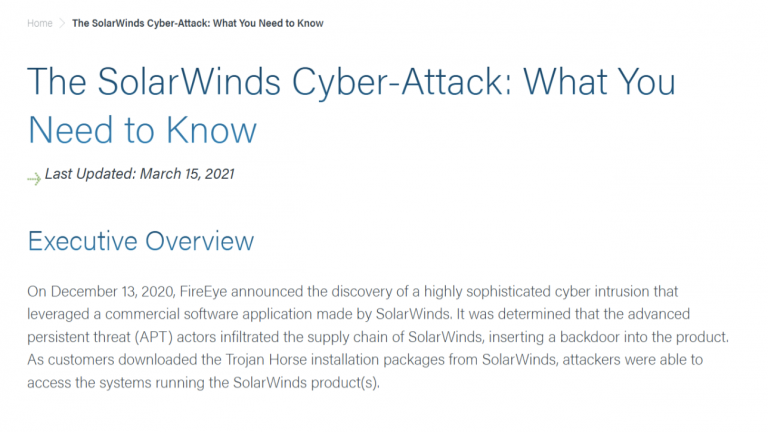
Relatable Case Study : SolarWinds (real-world security breach)
- Organisation: SolarWinds Corporation, a provider of IT management software used by organisations all over the world.
- Incident: In 2020, SolarWinds suffered a major supply chain attack, where threat actors compromised its Orion software. Attackers inserted a sophisticated ‘backdoor’ into the Orion updates, with the update being applied to thousands of customers. This enabled unauthorised access to sensitive data.
- Financial Implications: SolarWinds faced reputational damage, lost customers and incurred significant remediation cost. Legal and regulatory implications were also encountered.
- How it relates to Risk:
- Supply chain risk management – this example highlights how attackers could inject malicious code (undetected) into software being used by other organisations.
- Inadequate detection and response – malicious software can also evade security tools
- Source Information: https://www.cisecurity.org/solarwinds
General Guidance
- Identify and document risks to systems, services, and data (asset inventory management and a supplier management can be key to this)
- Use a structured assessment to evaluate likelihood, impact, and required controls
- Understand risk appetite and set acceptable risk levels
- Regularly review risks – especially after change and incidents
- Maintain records of assessments, decisions, and key actions taken
- Hold security certifications such as Cyber Essentials, Cyber Essentials Plus, and IASME Cyber Assurance
- Require similar certifications (or equivalent standards) throughout your supply chain and procurement processes
Recommended Actions
- Keep it simple and secure
- Use an appropriate risk assessment methodology to determine appropriate action
- Document and prioritise based on the risk assessment and your risk appetite
- Ensure appropriate security measures are in place (implement controls to treat or mitigate risk)
- Ensure risk is reviewed (at least) annually, following security incidents and aligned with significant change – with alignment for information security policy
- Hold cyber security related certifications for your own organisation and require them in your supply chain
- Seek guidance and support from a Certified Information System Security Professional (CISSP) – such as RB Consultancy Ltd
How We Help
At RB Consultancy Ltd, we support organisations by:
- Providing templates, guidance and experience to support
- Explaining what security measures are available and how they can help
- Collaborating to implement security controls
- Assessing and issuing certifications – such as Cyber Essentials, Cyber Essentials Plus and IASME Cyber Assurance
- Providing risk assessment advice and guidance
- Contact us for consultancy and certification support
Conclusion
Effective risk management can help avoid major security incidents – the SolarWinds case study helps to highlight a supply chain risk.
Regular risk assessments, clear ownership, and documented action plans help protects assets and support accountability. Organisations can embed risk into culture and extend out to their supply chain. A risk-based approach can help identify the specific security controls, measures and steps to take for any organisation of any size.
Certifications such as Cyber Essentials, Cyber Essentials Plus and IASME Cyber Assurance can help demonstrate security measures are in place. Public and private organisations are already requiring certification (such as Cyber Essentials) in their supply chain – a recent announcement has also been also made by UK Government for FTSE 350 to require Cyber Essentials in their supply chain.
RB Consultancy Ltd helps organisations understand the importance of risk – we support the implementation of appropriate measures to help build cyber resilience. We are an IASME Certification Body and NCSC Assured Service Provider who provide services to empower and protect organisations. Holding CISSP and ISO 27001 lead implementer certification, you can Contact Us for assistance with cyber security resilience.
This blog is written by Remo Belisari, Managing Director of RB Consultancy Ltd. He is an experienced cyber security professional and cyber advisor. Remo holds certifications in CISSP, ISSAP, ISO 27001, Cyber Essentials, IASME Cyber Assurance and Defence Cyber Certification. He has many years of experience in IT and cyber security. He has supported organisations worldwide. His work includes helping a Fortune 500 company in USA and 100+ organisations across the UK. The views in this blog are his own. They do not necessarily reflect the views of RB Consultancy Ltd, its clients, partners, or affiliates. The content is for general information only.
